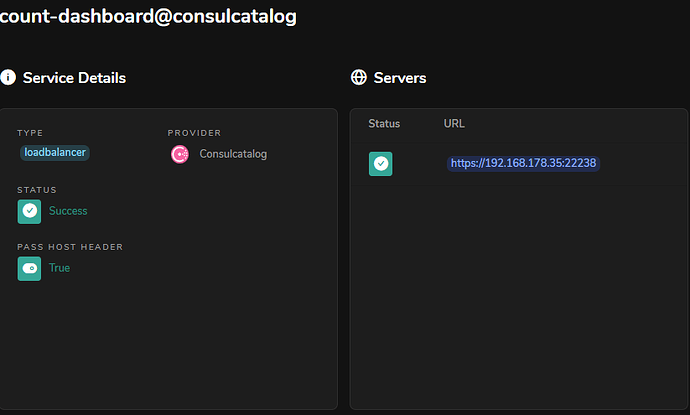
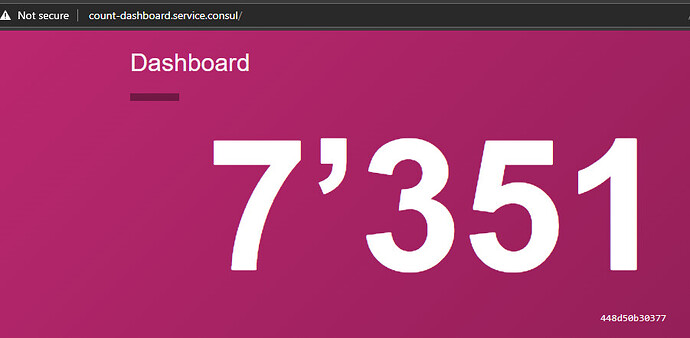
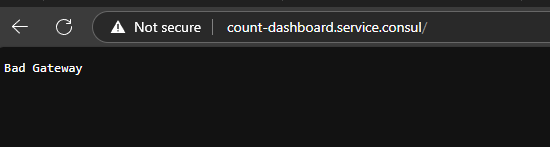
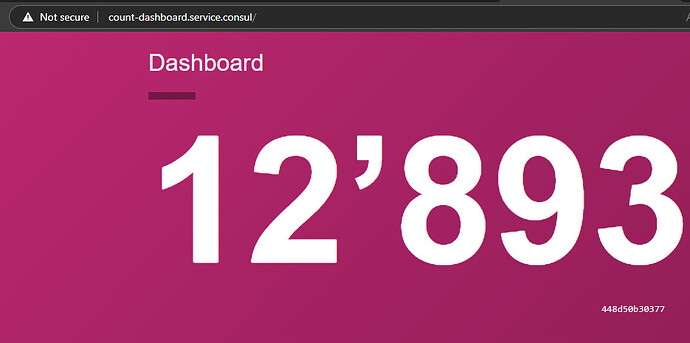
Hello, I am trying to get treafik with a sidecar working with ACL. The example works if am setting the intention count-dashboard -> count-api. But for traefik -> whoami this intention is not working. I need to set All -> whoami. The main difference I could find is that for whoami in consul no topology is shown. I was unable to set it via upstreams. I think this is the issue that consul is not allowing a connection from the proxy to the job. Does anybody know how to fix this?
traefik config
job "traefik" {
region = "global"
datacenters = ["dc1"]
type = "service"
group "traefik" {
count = 1
network {
mode = "bridge"
port "http-priv" {
static = 80
to = 80
host_network = "private"
}
}
service {
name = "traefik"
port = "http-priv"
connect{
native = true
}
tags = [
"traefik.enable=true",
"traefik.http.routers.dashboard.rule=Host(`traefik.test`)",
"traefik.http.routers.dashboard.service=api@internal",
]
}
task "traefik" {
driver = "docker"
config {
image = "traefik:latest"
ports = ["http-priv"]
volumes = [
"local/traefik.yml:/etc/traefik/traefik.yml",
"/home/test/consul/tls/consul-agent-ca.pem:/etc/traefik/consul-agent-ca.pem",
"/home/test/consul/tls/homelab-client-consul-3-key.pem:/etc/traefik/homelab-client-consul-3-key.pem",
"/home/test/consul/tls/homelab-client-consul-3.pem:/etc/traefik/homelab-client-consul-3.pem",
]
}
template {
data = <<EOF
entryPoints:
http-priv:
address: ':80'
log:
level: DEBUG
api:
dashboard: true
providers:
consulCatalog:
connectAware: true
prefix: traefik
exposedByDefault: false
endpoint:
address: 172.17.0.1:8500
scheme: http
token: {{key "nomad/namd-token"}}
tls:
caOptional: false
ca: /etc/traefik/consul-agent-ca.pem
cert: /etc/traefik/homelab-client-consul-3.pem
key: /etc/traefik/homelab-client-consul-3-key.pem
EOF
destination = "local/traefik.yml"
}
}
}
}
whoami config
job "whoami" {
datacenters = ["dc1"]
group "whoami" {
count = 1
network {
mode = "bridge"
port "web" {
host_network = "private"
}
port "connect-proxy-whoami" {
host_network = "private"
}
}
service {
name = "whoami"
port = "web"
connect {
sidecar_service {
}
}
tags = [
"traefik.enable=true",
"traefik.consulcatalog.connect=true",
"traefik.http.routers.whoami.rule=Path(`/whoami`)",
]
check {
type = "http"
path = "/health"
port = "web"
interval = "10s"
timeout = "2s"
}
}
task "whoami" {
driver = "docker"
config {
image = "traefik/whoami"
ports = ["web"]
args = ["--port", "${NOMAD_PORT_web}"]
}
resources {
cpu = 100
memory = 128
}
}
}
}